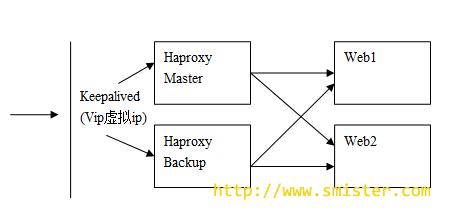
通过访问Keepalived的VIP(虚拟IP)来反问代理服务器Haproxy Master 来访问后端的web服务器, 当Haproxy Master 宕机 , 或者出现故障无法连接的时候 , Keepalived则会将VIP转移到Haproxy Backup ,通过Haproxy Backup访问后端的服务器
1、 分别在两台Haproxy分别安装配置Haporxy 和Keepalived
1) 安装Haproxy请查看Haproxy安装与配置(底下有链接) .
2) 安装Keepalived(2台机器都要)
[root@localhost ~]# cd /usr/local/src
[root@localhost ~]# wget http://www.keepalived.org/software/keepalived-1.2.8.tar.gz
[root@localhost ~]# tar zxvf keepalived-1.2.8.tar.gz
[root@localhost ~]# cd keepalived-1.2.8
[root@localhost ~]# ./configure --prefix=/usr/local/keepalived
[root@localhost ~]# make
[root@localhost ~]# make install
//基本配置
[root@localhost ~]# cp /usr/local/keepalived/sbin/keepalived /usr/sbin/
[root@localhost ~]# cp /usr/local/keepalived/etc/sysconfig/keepalived /etc/sysconfig/
[root@localhost ~]# cp /usr/local/keepalived/etc/rc.d/init.d/keepalived /etc/init.d/
[root@localhost ~]# mkdir /etc/keepalived
[root@localhost ~]# cp /usr/local/keepalived/etc/keepalived.conf /etc/keepalived/
//配置文件
(Haproxy Master)
[root@localhost ~]# vim /etc/keepalived/keepalived.conf
! Configuration File for keepalived
#发送邮件配置
global_defs {
notification_email {
398009951@qq.com
}
notification_email_from root@localhost.com
smtp_server 127.0.0.1
smtp_connect_timeout 30
router_id LVS_DEVEL
}
vrrp_instance VI_1 {
#该主机模式 , MASTER或BACKUP
state MASTER
#指定监听网卡
interface eth0
#虚拟id
virtual_router_id 51
#优先级 1~255, 从大到小排序
priority 100
advert_int 1
#认证模式
authentication {
auth_type PASS
auth_pass smister
}
#虚拟ip , 记得别冲突
virtual_ipaddress {
192.168.232.254/24 dev eth0 label eth0:0
}
}
(Haproxy Backup)
[root@localhost ~]# vim /etc/keepalived/keepalived.conf
! Configuration File for keepalived
#发送邮件配置
global_defs {
notification_email {
398009951@qq.com
}
notification_email_from root@localhost.com
smtp_server 127.0.0.1
smtp_connect_timeout 30
router_id LVS_DEVEL
}
vrrp_instance VI_1 {
#该主机模式 , MASTER或BACKUP , 注意这里是BACKUP机器
state BACKUP
#指定监听网卡
interface eth0
#虚拟id
virtual_router_id 51
#优先级 1~255, 从大到小排序 , 注意比MASTER小
priority 99
advert_int 1
#认证模式
authentication {
auth_type PASS
auth_pass smister
}
#虚拟ip , 记得别冲突 , 外国是通过该ip访问的
virtual_ipaddress {
192.168.232.254/24 dev eth0 label eth0:0
}
}
//Master和Proxy都开启keepalived服务
[root@localhost ~]# service keepalived start
2、 测试
1)在Master机器上查看是否生效
[root@localhost ~]# ip addr
1: lo: mtu 16436 qdisc noqueue state UNKNOWN
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 00:0c:29:9d:ca:1d brd ff:ff:ff:ff:ff:ff
inet 192.168.232.163/24 brd 192.168.232.255 scope global eth0
//这里绑定成功了
inet 192.168.232.254/24 scope global secondary eth0:0
inet6 fe80::20c:29ff:fe9d:ca1d/64 scope link
valid_lft forever preferred_lft forever
3: pan0: mtu 1500 qdisc noop state DOWN
link/ether 62:9f:a3:11:f3:80 brd ff:ff:ff:ff:ff:ff
2)测试连接
在浏览器中访问192.168.232.254 , 看是否能访问到后端的web , 如果可以证明实验成功了
3)我们试着将Master 的服务停掉 , 看keepalived是否能转移到Haproxy Backup中
(Master)
[root@localhost ~]# service keepalived stop
[root@localhost ~]# service haproxy stop
(Backup)
[root@localhost ~]# ip addr //查看是否生效
//再次通过浏览器访问 , 是否还生效 , 如果生效则证明成功了
3、 在生成环境中配置
[root@localhost ~]# vim /etc/rc.local
#添加词句
/usr/local/haproxy/sbin/haproxy -f /usr/local/haproxy/etc/haproxy.cfg
[root@localhost ~]# chkconfig --add keepalived
[root@localhost ~]# chkconfig keepalived on
//编写Master检测脚本,当Haproxy挂掉是 ,关闭keepalived , 让Haproxy Backup接管
[root@localhost ~]# vim /root/chkHaproxy.sh
#!/bin/bash
#
while :
do
status=`ps aux|grep haproxy | grep -v "grep" | wc -l`
if [ "$status" -eq 0 ];
then
/usr/local/haproxy/sbin/haproxy -f /usr/local/haproxy/etc/haproxy.cfg
sleep 2
status=`ps aux|grep haproxy | grep -v "grep" | wc -l`
if [ "$status" -eq 0 ];
then
/etc/init.d/keepalived stop
fi
fi
sleep 5
done
[root@localhost ~]# chmod +x /root/chkHaproxy.sh
[root@localhost ~]# nohup /root/chkHaproxy.sh &
好了.大功告成
版权声明:未经博主允许不得转载。http://smister.com/post-28.html